Home page
Quantum internet is impossible
Quantum entanglement is illusion
(Fig.1) Weak classical light wave surpassing the detection threshold of a photodetector after polarizing filters (= polarizers ) is measured to be a (fictional) photon.

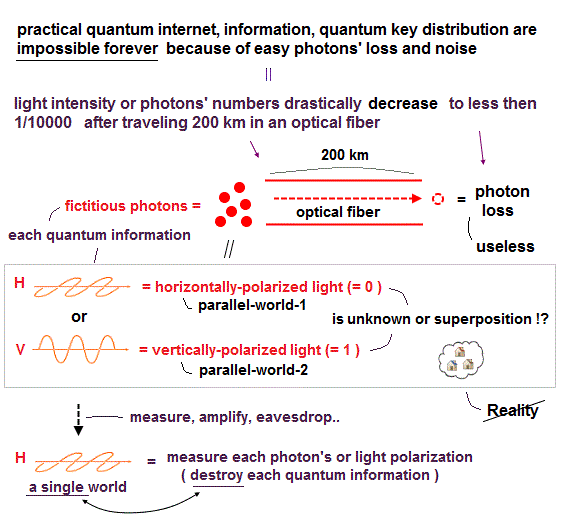
Quantum key distribution (= QKD ) is impractical, because its quantum information (= key ) is very weak classical light or a fictional photon, which is easily lost before reaching the receiver ( this p.1-left-1st-paragraph ).
Quantum information or quantum key (= photons ) can be explained by classical weak light with No quantum mechanics. = When the weak light or a (fictional) photon is disturbed or destroyed by eavesdroppers, this destroyed weak light or photon is used as a sign of eavesdroppers ( this-2nd-paragraph ).
This-How does QKD work ? says -- Quantum key = destroyed light
"Each photon encodes a bit of data in a quantum state. That state might represent polarization or phase. When the photons travel through a fiber or free-space channel, any attempt to measure them changes their properties. Which means interception can't happen without being noticed."
Even in the latest research in 2026, almost all fragile quantum information (= photons or quantum key ) was lost over just about 100km ( this-p.4-Fig.2C, p.5-Table II = quantum key rate becomes almost zero over just 100km ), which is impractical and cannot be amplified due to the stupid non-cloning quantum mechanical rule.
This-p.1-left-1st-paragraph says -- Useless quantum key
"In QKD systems,
single-photon serves as the carriers of quantum keys,
which cannot be amplified and are easily scattered or
absorbed by the transmission channel"
The present QKD or quantum cryptography is based on BB84 protocol in which when the sender sends vertically-polarized 0o (or horizontally-polarized 90o ) weak classical light or photon, and the receiver chooses the polarizing filter 0o (= called rectilinear basis ), the vertically-polarized 0o light passes (or horizontally-polarized 90o light reflects from ) the filter, which is measured to be a quantum key of 0 = pass (or 1 = reflect ), as shown in Fig.1-upper.
When the sender sends 45o-polarized (or 135o-polarized ) weak light or photon, and the receiver chooses the polarizing filter 45o (= called diagonal basis ), the 45o-polarized light passes (or 135o-polarized light reflects from ) the polarizing filter with 45o axis, which is measured to be a quantum key of 0 = pass (or 1 = reflect ), as shown in the middle of this Fig.1.
When the sender sends 45o-polarized light, and the receiver chooses the wrong polarizing filter with 0o axis, the 45o-polarized light splits into the pass and reflect sides of the filter, and is measured to be 0 (= pass ) or 1 (= reflect ) randomly, as shown in Fig.1-lower ( this-Figure.3, this 9th-paragraph, this p.3-1st~2nd-paragraphs ) obeying Malus law of the pass light intensity or probability proportional to I cos245o = 1/2 I (= half of the original light intensity I ).
↑ This case causes the random uncertain quantum key (= light pass =0 or reflect = 1 is random, uncertain ), which cannot be used as quantum key, so discarded after the receiver and the sender check whether they choose the right polarizing filter against the sent light polarization.
↑ Also when the distributor sends light with 0o or 90o polarization and the receiver chooses the polarizing filter with 45o axis, this case is discarded as wrong combination, due to giving random (= pass = 0 or reflect = 1 is uncertain ) keys.
So quantum keys are generated only when the receiver choosing the right polarizing filters (= axis 0o ) against the sent light's polarization (= vertical = 0o or horizontal = 90o ).
The cases of the receiver choosing polarizers with 45o axis when the distributor sending light with 45o or 135o polarization are also used as quantum keys.
↑ Polarizing filters whose axes are just parallel or perpendicular (= Not diagonal ) to the sent light's polarizations are the right choice.
When the intensity of the very weak (classical) light narrowly surpasses the detection threshold of the photodetector, it is detected as a (fictional) photon.
Even when the weak light with 45o polarization splits into pass and reflect sides of 0o polarizing filter, only one photon on one pass or reflect side can be detected, because the very weak light intensity further weakens by the filter (= a part of light is lost ), and it is unlikely that the split very weak light intensity can surpass two photodetector's detection thresholds in both sides of the filter simultaneously.
Even if eavesdroppers intercepts the light or photon, the eavesdroppers don't know what polarizing filters or bases are chosen by the receiver, so the eavesdropper who may measure the polarized light (= ex. 0o-polarized light ) by the wrong different filter (= 45o-polarizing filter ) is likely to get and re-send the wrong quantum key toward the receiver (= pass 0 or reflect 1 randomly ). ← The receiver's quantum keys are unknown to eavesdroppers. ( this 11~12th-paragraphs, this middle ).
As shown here, the classical weak light (+ photodetectors ) can naturally explain the present quantum key distribution, and quantum mechanical fictional photon or (fantasy) superluminal entanglement is unnecessary.
QKD is said to use the impossibility of copying quantum photon (= this 2. No cloning theorem of quantum mechanics ) as a reason for the secure quantum key, but in fact, this quantum mechanical no cloning theorem is unnecessary in the QKD.
Even if the eavesdropper can intercept (= measures ) the light (or photon ), copy and resend it towards the receiver, there is always a detectable time lag or delay in the eavesdropper copying and resending the same light (= which takes extra time ), which time lag can be easily detected as an evidence of eavesdropping. ← Quantum mechanical no-cloning theorem is unnecessary in QKD.
So quantum mechanics or no-cloning theorem is unnecessary in the current (useless) quantum key distribution. Classical weak light can naturally explain the current quantum key distribution, so quantum mechanics is useless.
(Fig.2) 99.995% of all fragile quantum information or photons are lost over just 130km. ←quantum network is completely useless.

Quantum communication or quantum key distribution (= QKD ) is impractical, deadend, still unable to send the fragile quantum information or photons over 80km stably as shown in the recent hopeless QKD research in 2024 ( this 7th-paragraph ).
↑ This research paper in the recent QKD ↓
p.1-abstract says -- Almost all photons were lost
"Utilising the 79 km long.... secret key bits per pulse of 4.8 × 10−5 " ←The probability of a photon (= quantum information bit ) reaching the destination is extremely low = just 0.000048 (= 99.995% of all information or photon pulses are lost over just 79km )
p.7-Fig.4 shows -- No longer than 150km
this current quantum key distribution cannot send the fragile quantum information over 150km where bits (= quantum key generation ) per pulse is zero.
↑ Quantum key distribution sending information key over practically-long distance
is impossible (forever).
Quantum internet or communication needing the zero-loss of information is much more impossible.
(Fig.3) The probability of each fragile quantum information or a photon transmitted over 500km (× 2 ) is hopelessly low = just 0.000000000003 (= almost all photons are lost ), which is unrealistic.

The 3rd paragraph of this news (in 2023 ) says -- massive photon loss
The recent achievement by Chinese scientists has pushed this limit to 1,002 kilometres (= two persons sent each photon over 500km towards the center point between them ), with a secure key rate of 0.0034 bits per second (= too few and too slow )."
↑ This rate of getting quantum key is too slow (= only one bit or one photon reaching the destination per 300 seconds = 0.0034 bits/second ) to be a practical quantum key distribution that needs a key-generation rate of at least megabits per seconds ( this-middle-Challenge of QKD ).
↑ This research paper ↓
p.1-abstract says -- Almost all quantum key is lost
"The secure key rate is 3.11 × 10–12 per pulse" ← The probability of a fragile quantum information or a photon reaching the destination over 1000km per one sent photon pulse is just 0.00000000000311 (= 99.9999999997% of all photons were lost ).
p.3-Fig.1 and p.4-right says -- No longer than 500km
"The fibre distances between Alice-Charlie and Bob-Charlie are measured to be
500 km and 502 km" ← Alice and Bob sent their photons over about 500km towards the center Charlie.
p.5-left-3rd-paragraph says -- Error-prone quantum key
"The quantum bit error rate (QBER)... is measured to be 4.20%" ← Even photons reaching the destination showed the error rate of 4.20%, which cannot be used as reliable quantum keys after all.

Feel free to link to this site.